Webmin is one of the popular web-based interfaces for system administration for Unix. We can manage the system services using the appropriate Webmin modules. The popular and official modules available for Webmin includes cron, bind8, apache, mysql, dovecot, postfix, postgrey, fail2ban, and syslog. We can install these modules based on the actual needs and manage the associated services from the Webmin itself without using the shell. Webmin makes it easy to administer the system using the graphical interface. The most recent version of Webmin while writing this tutorial is 1.930. We will install the same as part of this tutorial.
This tutorial provides the steps required to install Webmin on the popular Linux distribution Ubuntu and access it via Apache by configuring it as reverse proxy. In this way, we will install Webmin and access it via Apache over the standard HTTP/HTTPS ports. It provides all the steps required to install and use Webmin on Ubuntu 18.04 LTS. The steps should be similar for other Linux systems and Ubuntu versions.
You may also follow the relevant tutorials including How To Install Apache 2 On Ubuntu 18.04 LTS, Configure Virtual Host On Apache and How To Install Let’s Encrypt For Apache On Ubuntu.
Ubuntu Server – You have root access or permissions to use sudo on the Ubuntu Server to continue with this tutorial.
Apache Web Server – It assumes that the Apache is already installed on the system and it’s configured properly to access the Virtual Host using the domain name. It can be easily done on your local system in case you have a static IP address. You can also follow How To Install Apache 2 On Ubuntu 18.04 LTS to install the Apache Web Server.
Firewall – Make sure that the ports 80 and 443 are open.
Domain – You must also own a domain to continue with this tutorial. It assumes that the domain record is configured for the server and it’s pointing to the correct IP address.
Apache Modules – As part of this tutorial, also make sure that the appropriate apache modules are enabled as shown below.
# Enable rewrite modulesudo a2enmod rewrite# Enable SSL modulesudo a2enmod ssl# Enable Proxy modulesudo a2enmod proxy_http# Restart Apachesudo systemctl restart apache2In this section, we will add the virtual host and enable it to access the application using the domain. You may skip this step in case you already have an active website or application accessible from the browser using the domain name.
Add and update the Virtual Host to Apache web server as shown below. I have used the nano editor for demonstration purposes. You can use any editor of your choice. Also, replace example.com with the actual domain. Create the directory /var/www/example.com/html to store the website or application files and /var/www/example.com/logs for website specific logs.
# Add Virtual Hostsudo nano /etc/apache2/sites-available/example.com.conf# ContentServerName example.comServerAlias www.example.comServerAdmin admin@example.comDocumentRoot /var/www/example.com/htmlOptions -Indexes +FollowSymLinksDirectoryIndex index.htmlAllowOverride AllRequire all grantedErrorLog /var/www/example.com/logs/error.logCustomLog /var/www/example.com/logs/access.log combined# Save and exit the editorSave the file using the Nano text editor by pressing CTRL + O, then press Enter to write the file. Press CTRL + X to close the editor. Now enable the virtual host as shown below. Make sure that the directory /var/www/example.com/html and /var/www/example.com/logs exists.
# Create directoriessudo mkdir -p /var/www/example.com/htmlsudo mkdir -p /var/www/example.com/logs# Optionally disable default configurationsudo a2dissite 000-default# Test configurationsudo apache2ctl configtest# OutputSyntax OK# Enable virtual hostsudo a2ensite example.com# OutputEnabling site example.com.To activate the new configuration, you need to run:systemctl reload apache2# Test configurationsudo apache2ctl configtest# OutputSyntax OK# Reload Apachesudo systemctl reload apache2Now add the index.html file having content as shown below.
# Add index.htmlsudo nano /var/www/example.com/html/index.html# ContentMy DomainWelcome to My Domain.
# Save and exit the editorIf your domain is correctly pointing to your system, you must be able to access it from the browser by navigating to http://www.example.com/index.html. It should show the output of our simple HTML file – Welcome to My Domain.
In this section, we will install the most recent version of Certbot using the official repository. You may uninstall the previous installation of Certbot using the commands as shown below.
# Uninstall Certbotsudo apt remove python-certbot-apachesudo apt remove certbotsudo apt purge certbotsudo apt-get autoclean# Make sure to use purge - it will clean all configuration filessudo apt-get autoremove# ORsudo apt-get --purge autoremoveNow we will add the official repository to the system repositories. It can be done using the commands as shown below.
# Add Certbot repositorysudo add-apt-repository ppa:certbot/certbot# Press Enter to confirm This is the PPA for packages prepared by Debian Let's Encrypt Team and backported for Ubuntu(s). More info: https://launchpad.net/~certbot/+archive/ubuntu/certbotPress [ENTER] to continue or Ctrl-c to cancel adding it.......Now refresh the packages index using the command as shown below.
# Refresh packages indexsudo apt-get updateWe can install the Certbot using the command as shown below.
# Install Let's Encryptsudo apt-get install python-certbot-apache# Installation results......Setting up python3-certbot-apache (0.31.0-1+ubuntu18.04.1+certbot+1) ...Setting up python-certbot-apache (0.31.0-1+ubuntu18.04.1+certbot+1) ...Processing triggers for systemd (237-3ubuntu10.29) ...Processing triggers for man-db (2.8.3-2ubuntu0.1) ...Processing triggers for ufw (0.36-0ubuntu0.18.04.1) ...Processing triggers for ureadahead (0.100.0-21) ...Processing triggers for libc-bin (2.27-3ubuntu1) ...We can confirm the installation by checking the Certbot version as shown below.
# Check Certbot versioncertbot --version# Outputcertbot 0.31.0This is how we can clean the existing installation of Certbot and install the most recent version of it on the system.
We will install the SSL certificate and secure virtual host in this step. It can be done using the command as shown below.
# Install Certificate - Syntax - Single Domainsudo letsencrypt --apache -d--email # Install Certificate - Syntax - Multiple Domainssudo letsencrypt --apache -d ,, --email # Examplesudo letsencrypt --apache -d example.com,www.example.com --email admin@example.com# Agree - Press A and Enter - First time onlySaving debug log to /var/log/letsencrypt/letsencrypt.logPlugins selected: Authenticator apache, Installer apache- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -Please read the Terms of Service athttps://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You mustagree in order to register with the ACME server athttps://acme-v02.api.letsencrypt.org/directory- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -(A)gree/(C)ancel: A# Share Email for communication - Press Y and Enter- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -Would you be willing to share your email address with the Electronic FrontierFoundation, a founding partner of the Let's Encrypt project and the non-profitorganization that develops Certbot? We'd like to send you email about our workencrypting the web, EFF news, campaigns, and ways to support digital freedom.- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -(Y)es/(N)o: Y# Choose redirect options - redirectPlease choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access.- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -1: No redirect - Make no further changes to the webserver configuration.2: Redirect - Make all requests redirect to secure HTTPS access. Choose this fornew sites, or if you're confident your site works on HTTPS. You can undo thischange by editing your web server's configuration.- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 2# Certificate installed successfullyCongratulations! You have successfully enabled https://example.comYou should test your configuration at:https://www.ssllabs.com/ssltest/analyze.html?d=example.com- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/example.com/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/example.com/privkey.pem Your cert will expire on 2020-01-01. To obtain a new or tweaked version of this certificate in the future, simply run certbot again with the "certonly" option. To non-interactively renew *all* of your certificates, run "certbot renew" - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF:https://eff.org/donate-leNow if you try to open the URL – http://www.example.com/index.html, it must redirect you to https://www.example.com/index.html. Make sure that your firewall allows communication on port 443.
This is how we can secure an entire website or application using the SSL certificate for secure communication over the Apache web server and the clients(Browser etc).
Now if you again open the virtual host file, you must see the redirection lines at the bottom of your host.
# Check Virtual Hostsudo nano /etc/apache2/sites-available/example.com.conf# Scroll down........RewriteEngine onRewriteCond %{SERVER_NAME} =www.example.comRewriteRule ^ https://%{SERVER_NAME}%{REQUEST_URI} [END,NE,R=permanent]The rewrite rule redirects all the HTTP requests to HTTPS.
The Certbot client also creates the SSL virtual host and enable it as part of the SSL installation process. You can check it’s content as shown below.
# Check SSL Virtual Hostsudo nano /etc/apache2/sites-available/example.com-le-ssl.conf# ContentServerName example.comServerAlias www.example.comServerAdmin admin@example.comDocumentRoot /var/www/example.com/htmlOptions -Indexes +FollowSymLinksDirectoryIndex index.phpAllowOverride AllRequire all grantedErrorLog /var/www/example.com/logs/error.logCustomLog /var/www/example.com/logs/access.log combinedSSLCertificateFile /etc/letsencrypt/live/example.com/fullchain.pemSSLCertificateKeyFile /etc/letsencrypt/live/example.com/privkey.pemInclude /etc/letsencrypt/options-ssl-apache.confThe Cerbot configures your SSL virtual host as shown above.
The SSL certificates issued by Let’s Encrypt expires after 90 days from the date of installation. The good point is that the Certbot installed by us from the official repository checks for renewal twice a day using the system timer. The auto-renewal feature on non systemd timer is provided by a cron script placed in /etc/cron.d. It renews the certificates that are about to expire in the next 30 days.
You can also test the renewal process by simulating the renewal command as shown below.
# Simulate renewal commandsudo certbot renew --dry-runThe above command will show the logs having messages to get an idea about how it will be run for actual renewal. We can also run the command manually to renew the certificates that are about to expire in the next 30 days.
# Renew certificatessudo certbot renew# Renewal messagesSaving debug log to /var/log/letsencrypt/letsencrypt.log- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -Processing /etc/letsencrypt/renewal/example.com.conf- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -Cert not yet due for renewal- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -The following certs are not due for renewal yet:/etc/letsencrypt/live/example.com/fullchain.pem expires on 2020-01-01 (skipped)No renewals were attempted.- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -The Apache service must be reloaded after certificate renewal. We can do it by appending –renew-hook “systemctl reload apache2” to the /etc/cron.d/certbot file as shown below.
# Append renew hook0 */12 * * * root test -x /usr/bin/certbot -a \! -d /run/systemd/system && perl -e 'sleep int(rand(43200))' && certbot -q renew --renew-hook "systemctl reload apache2"Now again do a dry run by simulating the renewal command as shown below.
# Simulate renewal commandsudo certbot renew --dry-runIt should run successfully to ensure that the certificates will be automatically renewed before the expiry.
In this step, we will install Webmin using the official repository on both Debian and non-Debian based systems. We can install Webmin using the Webmin APT repository on Ubuntu as shown below. I have used the nano editor for demonstration purposes. You can use any editor of your choice.
# Add repositorysudo nano /etc/apt/sources.list# Add these lines at lastdeb http://download.webmin.com/download/repository sarge contribdeb http://webmin.mirror.somersettechsolutions.co.uk/repository sarge contrib# Save and exit the editorSave the file using the Nano text editor by pressing CTRL + O, then press Enter to write the file. Press CTRL + X to close the editor.
Install the GPG key as shown below. We need the GPG key to trust the repository.
# Navigate to your preferred directorycd ~# Download the GPG Keywget http://www.webmin.com/jcameron-key.asc# Add the Keysudo apt-key add jcameron-key.asc# OutputOKNow we can install the most recent version of Webmin as shown below.
# Refresh the packages indexsudo apt-get update# Install Webminsudo apt-get install webmin -y# Installation logsSetting up webmin (1.930) ...Webmin install complete. You can now login to https://ip-xx-xx-xx-xx:10000/as root with your root password, or as any user who can use sudoto run commands as root.Processing triggers for man-db (2.8.3-2ubuntu0.1) ...Processing triggers for mime-support (3.60ubuntu1) ...Processing triggers for ureadahead (0.100.0-21) ...Processing triggers for systemd (237-3ubuntu10.29) ...You can test the Webmin in case port 10000 is open, else simply skip this section and continue with the next section.
We can directly access the Webmin using the URL – https://xx.xx.xx.xx:10000 in case port 10000 is opened. Make sure to replace the xx.xx.xx.xx with your actual IP. It will show the security risk warning as shown in Fig 1.
Fig 1
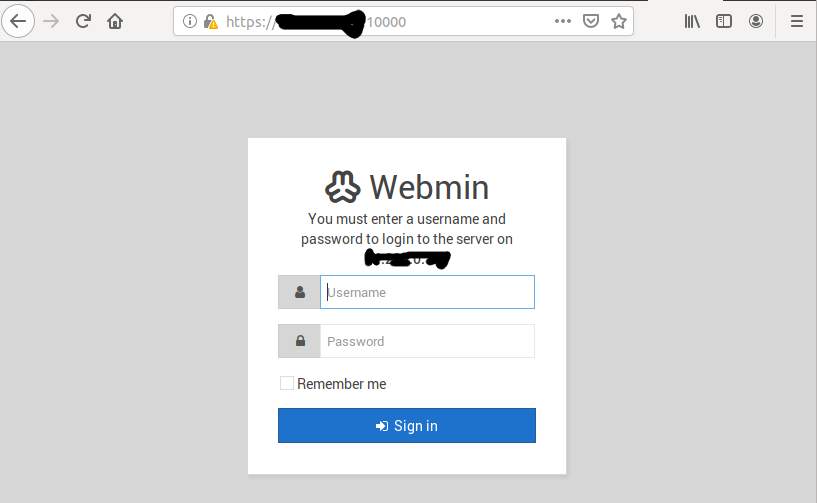
Accept the risk and continue to access Webmin. It will show the login screen as shown in Fig 2.
Fig 2
Now login to Webmin using your root or sudo user credentials. You can also change the root credentials for Webmin using the command as shown below.
# Change Webmin passwordsudo /usr/share/webmin/changepass.pl /etc/webmin# Examplesudo /usr/share/webmin/changepass.pl /etc/webmin root pass123The above command will change the root user password for Webmin. Now login to your Webmin. It will show the dashboard as shown in Fig 3.
Fig 3
We will access the Webmin by configuring reverse proxy on port 80/443 as a regular web app by configuring the webserver. This will avoid opening an additional port for Webmin i.e. 10000 and maintaining SSL certificate for Webmin. It can be done for the Apache Web Server as shown below.
# Update SSL Virtual Hostsudo nano /etc/apache2/sites-available/example.com-le-ssl.conf# ContentServerName example.comServerAlias www.example.comServerAdmin admin@example.comProxyPass / http://localhost:10000/ProxyPassReverse / http://localhost:10000/ErrorLog /var/www/example.com/logs/error.logCustomLog /var/www/example.com/logs/access.log combinedSSLCertificateFile /etc/letsencrypt/live/example.com/fullchain.pemSSLCertificateKeyFile /etc/letsencrypt/live/example.com/privkey.pemInclude /etc/letsencrypt/options-ssl-apache.conf# Save and exit the editorYou must enable the proxy_http module of the Apache Web Server as shown below.
# Enable Proxysudo a2enmod proxy_http# Test configurationsudo apache2ctl configtest# Reload Apachesudo systemctl reload apache2We also need to configure Webmin to accept connections from Apache as shown below. Also, make sure to use the FQDN or the domain name used to access the website. We can configure Webmin for the primary domain as shown below.
# Update configsudo nano /etc/webmin/config# Add at last..........referers=example.com# Save and exit the editorUpdate miniservsudo nano /etc/webmin/miniserv.conf# Configure SSL...ssl=0......ssl_redirect=0# Save and exit the editor# Restart Webminsudo systemctl restart webminNow we can access Webmin using the primary domain by redirecting to https://www.example.com. It will show the login screen as shown below.
Fig 4
We must update the SSL certificate in order to support the subdomain. It can be done using the command as shown below. Let’s Encrypt allows up to 100 domains for a single SSL certificate.
# Install Certificate - Syntax - Single Domainsudo letsencrypt --apache -d example.com,www.example.com,sub1.example.com --email admin@example.comWe can configure the Apache server to access the Webmin over a subdomain. In this way, we can access the website over the main domain and access the Webmin over a subdomain. It can be done for the Apache Web Server as shown below.
# Update SSL Virtual Hostsudo nano /etc/apache2/sites-available/sub1.example.com-le-ssl.conf# ContentServerName example.comServerAlias sub1.example.comServerAdmin admin@example.comProxyPass / http://localhost:10000/ProxyPassReverse / http://localhost:10000/ErrorLog /var/www/example.com/logs/error.logCustomLog /var/www/example.com/logs/access.log combinedSSLCertificateFile /etc/letsencrypt/live/example.com/fullchain.pemSSLCertificateKeyFile /etc/letsencrypt/live/example.com/privkey.pemInclude /etc/letsencrypt/options-ssl-apache.conf# Save and exit the editor# Test configurationsudo apache2ctl configtest# Enable subdomainsudo a2ensite sub1.example.com-le-ssl# Reload Apachesudo systemctl reload apache2We also need to configure Webmin to accept connections from Apache as shown below. We can configure Webmin for the subdomain as shown below.
# Update configsudo nano /etc/webmin/config# Add at last..........referers=sub1.example.com# Save and exit the editorUpdate miniservsudo nano /etc/webmin/miniserv.conf# Configure SSL...ssl=0......ssl_redirect=0# Save and exit the editor# Restart Webminsudo systemctl restart webminNow we can access Webmin using the subdomain by redirecting to https://sub1.example.com.
We can configure the Apache server to access the Webmin over the subdirectory. In this way, we can access the website over the main domain and access the Webmin over the sub URL. It can be done for the Apache Web Server as shown below.
# Update SSL Virtual Hostsudo nano /etc/apache2/sites-available/example.com-le-ssl.conf# ContentServerName example.comServerAlias www.example.comServerAdmin admin@example.comProxyPass /webmin/ http://localhost:10000/ProxyPassReverse /webmin/ http://localhost:10000/DocumentRoot /var/www/example.com/htmlOptions -Indexes +FollowSymLinksDirectoryIndex index.phpAllowOverride AllRequire all grantedErrorLog /var/www/example.com/logs/error.logCustomLog /var/www/example.com/logs/access.log combinedSSLCertificateFile /etc/letsencrypt/live/example.com/fullchain.pemSSLCertificateKeyFile /etc/letsencrypt/live/example.com/privkey.pemInclude /etc/letsencrypt/options-ssl-apache.conf# Save and exit the editor# Test configurationsudo apache2ctl configtest# Reload Apachesudo systemctl reload apache2We also need to configure Webmin to accept connections from Apache as shown below. We can configure Webmin for the subdirectory as shown below.
# Update configsudo nano /etc/webmin/config# Add at last..........relative_redir=0referers=example.comwebprefix=/webminwebprefixnoredir=1# Save and exit the editorUpdate miniservsudo nano /etc/webmin/miniserv.conf# Configure SSL...ssl=0......ssl_redirect=0# Save and exit the editor# Restart Webminsudo systemctl restart webminNow we can access Webmin using the subdirectory by redirecting to https://www.example.com/webmin/.
This is how we can install Webmin and access it over the primary domain, subdomain, and subdirectory by configuring the Apache Web Server as a reverse proxy.
PREV: Get started, install, and configure the License Server
NEXT: Specify a License Server for an RD Session Host Server to Use